Trusted Future is a think and do tank working to elevate trust in today’s digital ecosystem. We bring together experts, advance new research, highlight best practices, policies and recommendations, and explore new ways to foster and enhance the basic trust we need to support and sustain a healthier digital ecosystem.
Trusted Future congratulates NTIA for inviting public comment on these thoughtful and important questions. We write to provide comments on two specific questions, Questions 17 and 18. As detailed below, given the importance of elevating trust (security, privacy, function) in technology to help advance important consumer gains, our main focus in these comments is to encourage NTIA, other stakeholders, and policymakers to apply a ‘trust screen’ to any proposed policies or questions, and ask a simple question – would this policy enhance or undermine trust in hardware, software, products, services or the digital ecosystem?
Trusted Future believes it is critical for the information infrastructure of today, and obtaining the benefitsof the emerging technology of tomorrow, to have a vibrant digital ecosystem that is trusted, responsible, inclusive, and safe — one where you can trust that your privacy will be protected, your data will be secured, your safety can be guaranteed, and that advancements in technology will lead to a more just, equitable and inclusive society.
We’ve already seen how the mobile app ecosystem has delivered tremendous opportunities and transformed our lives in ways few could have predicted. With a new set of emerging technologies just over the horizon that enable breakthrough connected opportunities throughout more parts of the economy, app ecosystem benefits are poised to become even more pervasive, and their impacts even more profound. These technologies of the future have the potential to foster previously unthinkable opportunities to improve our lives and help solve critical societal challenges in ways not possible before. For example, experts predict that new and emerging technologies can help us tackle our climate challenges, bend the healthcare cost curve, make farmers more productive, and our economy more prosperous. According to Accenture’s economic modeling analysis, this mobile future will drive up to $2.7 trillion in additional gross output growth between 2021 and 2025, could add $1.5 trillion to U.S. GDP, help create 16 million jobs, and enable people to do things never before possible.
But it is also become increasingly clear that we risk missing or delaying these transformational opportunities if people lack the foundational trust in the technologies needed to deliver it, or if companies and individuals don’t adopt new technologies because they can’t trust that their privacy will be protected, and their security preserved.
As our mobile devices and the associated app ecosystem have become even more essential as the gateway to so many of these opportunities, recent Trusted Future consumer surveys underscore the importance of fostering trust in the mobile app ecosystem in order to achieve its full potential. We support the Administration’s goal of driving a dynamic, innovative, competitive and secure mobile ecosystem that can maximize user benefits and opportunity, and thank NTIA for the opportunity to share our work and perspective as it relates to the mobile app ecosystem.
TRUSTED FUTURE’S RESPONSE TO QUESTIONS 17 AND 18.
To get a clearer picture of the privacy and security landscape, Trusted Future commissioned a survey conducted by the research firm AudienceNet of 2,051 Americans in October 2021. Trusted Future and the National Security Institute also separately surveyed nearly 3,200 consumers to gauge their technology usage habits as it relates to privacy and security.
The surveys found that mobile devices have emerged as a primary gateway to the broader digital ecosystem we connect to, with more people owning mobile computing devices than laptops or desktop computers. They have become essential in our daily lives. Our mobile devices are often the last thing we check when we go to bed and the first thing we check when we wake up. Its why nearly half of American’s say their phone is their most valuable possession.
We were not surprised to learn from our surveys that smartphones are so essential to some that 21% said that they would prefer to have a root canal rather give up their smartphone for a week. Incredible technological advances in mobile devices and the apps they enable have made it possible for us to use our mobile devices in incredible ways – allowing us to check bank accounts from anywhere, monitor our health and fitness, engage in intimate private conversations, and control our smart homes.
When using these apps, consumers want to keep their mobile device data private and their devices secure. Mobile devices are quickly becoming the first line of defense against cyberattacks and malware, and with the advent of privacy nutrition labels, tools to prevent app tracking, and comprehensive app store privacy reviews, one of the most important pathways for privacy protection. As smartphones become more ubiquitous, they have also become essential throughout more parts of our lives, and the need to be able to trust that they can protect our privacy and security has risen commensurately.
BASELINE PRIVACY PROTECTIONS ARE ESSENTIAL FOR FOSTERING A TRUSTED APP ECOSYSTEM
Consumers are eager to protect many different kinds of sensitive data on their phones. When asked what types of personal information they keep on their phones that they want to make sure they have the tools to protect, consumers responded:
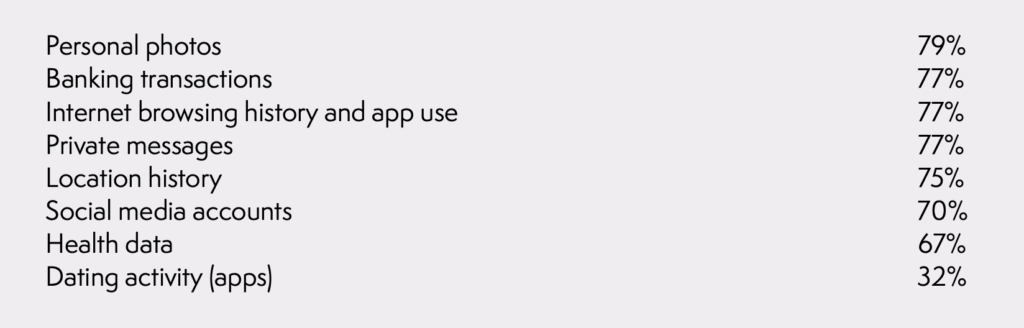
Given the types of sensitive information people use with their devices, respondents indicated they were more concerned about protecting personal data on a smartphone than on a laptop computer.
The surveys also found that Americans want companies to do more to protect their personal data online. Whether it was banking transactions, health data, information about their children, or photos, about 8 out of 10 respondents want technology companies to do more to keep that information protected. And virtually no one wants these companies to do less. These numbers were consistent across age, race, and income demographics.
There are a variety of elements that can help improve privacy protection and thus elevate a more trusted app ecosystem that is important for consumers. Take for example the very popular App Tracking and Transparency Features and privacy nutrition label features now being implemented by major app stores – features that cannot be achieved on a device alone or consistently across apps absent app store policies that enforce these features. Our consumer surveys suggest these are privacy features that consumers strongly support.
Our survey found:
APP TRACKING: 68% SUPPORT THE ABILITY TO OPT OUT OF TRACKING OF THEIR ONLINE ACTIVITIES. Giving users choice about whether they want to be tracked across apps and websites by advertisers and allowing them to choose whether data is collected about them are key elements of building trust and returning a sense of consumer control over their personal data. App Tracking Transparency features have found, unsurprisingly, that very few consumers choose to allow apps to track them online. There are a variety of ways people can be surreptitiously tracked online, their private data collected, which then may be auctioned by data brokers. According to one provider, the average mobile app has six embedded trackers from third-party companies for the sole purpose of collecting and tracking people and their personal information. It has led to expanded consumer interest in a more trusted digital ecosystem where privacy protection can be a basic digital right, where clear boundaries exist around what is collected, processed, tracked and shared, and where users have the tools they need to control their own data. Policymakers should continue to encourage privacy protecting features and implementations.
PRIVACY LABELS: 64% OF PEOPLE WANT THE ABILITY TO KNOW ABOUT THE DATA THAT IS BEING COLLECTED ABOUT THEM. In addition to states like California that have recently adopted laws to give consumers such access, mobile phone app stores have also now created mandatory “privacy labels” for each app which allows users to learn about the data the app may collect, and whether that data is linked to them or used to track them. Because the labels are in an easy-to-understand form, they can be used to quickly compare the data handling protections between seemingly similar apps, or to identify if the application is collecting extraneous information unrelated to the purpose of the app. App privacy nutrition labels, which can’t be enforced on the devices alone, but only through the app store review process, give consumers critical information to let them know for each app the data that is collected, for what purpose, and help users understand whether they can trust a specific app. In fact, our survey found 56% want even greater transparency about how companies use their personal data online. Policy makers should continue to support greater transparency about the types of data being collected, and how it is used to help consumers make more informed choices.
BASELINE SECURITY PROTECTIONS ARE ESSENTIAL FOR FOSTERING A TRUSTED APP ECOSYSTEM
As the President’s Executive Order on Improving the Nation’s Cybersecurity explains: “In the end, the trust we place in our digital infrastructure should be proportional to how trustworthy and transparent that infrastructure is, and to the consequences we will incur if that trust is misplaced.” Building trust in the app ecosystem by elevating robust security is essential for achieving its full potential. However, our survey found that 58% of respondents lack trust in the security of the technology they use, and our survey found that more than 9 in 10 respondents are concerned about being adequately protected from malware, ransomware, and viruses.
We believe security needs to be a foundational design element built into systems at every level. This will foster agile solutions across the ecosystem that embrace best practices standards, enable continuous innovation in cyber-defenses, advance globally recognized frameworks, and should be underpinned by smart government policies to keep personal and business data secure and our economy moving forward.
Greater adoption of basic cyber hygiene steps, like the FTC’s Tips to Protect Your Privacy on Apps could tremendously help protect users’ privacy – which for example suggests that to better protect your privacy and security consumers should use official app stores, check what information the app will access before they are downloaded, and pay attention to the permissions that apps ask for.
It’s clear consumers are not doing enough on their own, and they need companies that make up the app ecosystem to provide baseline security protections as a design attribute. Our survey, consistent with other findings, demonstrated that Americans continue to fall short when it comes to maintaining basic cyber hygiene practices. But it’s also clear that they trust device manufacturers the most to protect them. When asked who they trust most to protect and maintain privacy and safety online, respondents indicated:

Consumers also prefer that the technologies they use be built with robust security standards that can protect them from hackers, malware, and other threats built into the system by design, according to 50% of respondents. That is compared to 28% who prefer the option to install security protections later.
To build a more trusted future, consumers need 21st century consumer safeguards that can protect all of us from malicious, fraudulent, and unethical actors that seek to deceive, harm, or exploit our trust. The NIST Cybersecurity Framework illustrates how layers of security solutions should work together to minimize the risk of cyberthreats, and improve the robustness of our technology systems. It’s also important to have a layered approach to building trust throughout the mobile app ecosystem – by device manufacturers, by app developers, by cloud providers and everyone else throughout the entire software supply chain. They all play central roles in fostering a trusted, competitive, and innovative mobile app ecosystem.
As President Biden has explained in calling on the private sector to “lock their digital doors” before Russia gets in, “[w]e need everyone to do their part to meet one of the defining threats of our time.” Everyone includes app developers, device manufacturers, operating system developers, and app store providers. As Michael Chertoff, the former Secretary of Homeland Security has explained, “App stores have become a central part of the modern software supply chain,” and need to employ a base level of security review that also involves human review to minimize the security risks posed by apps from untrustworthy sources or that harness untrustworthy techniques.
However, we are also facing a severe shortage of cyber workers at a time when we need them the most. App developers and startups often can’t hire the security professionals they need. To build robust security throughout the app ecosystem, industry needs the cyber talent necessary to do thorough reviews. However, just last Spring the Commerce Department found that there were half a million unfilled cyber jobs in the U.S. alone, and another survey estimated over 3.5 million globally. The need for cybersecurity skills is only going to grow. To drive a trusted and secure app ecosystem, we support the Administration’s “whole of nation” efforts to invest in and build the cyber talent necessary to enable app developers, device manufacturers and everyone throughout the app economy supply chain to gain access to the cyber talent they need.
APP STORES PLAY A CRITICAL ROLE IN ENABLING A TRUSTED APP ECOSYSTEM
One of the primary vehicles for reviewing the privacy and security of apps is the app store review processes. Each of the millions of apps now available in official app stores has been through an app vetting process for compliance with a suite of security, privacy, and other policies designed to protect users from harm and/or to improve their experience, and are constantly monitored, updated, and removed when necessary to provide a critical level of trustworthiness.
By adopting and enforcing rigorous policies, app stores create trusted marketplaces that app developers can rely upon, and consumers can trust. This is essential because trust is a prerequisite for encouraging consumers to try new apps, that may enable new opportunities or deploy new types of business models, but come from unknown developers, a hallmark of the app economy.
While the number of mobile apps has grown exponentially year over year, it is also true that millions of apps and app updates are rejected each year by official app stores because they violate privacy guidelines, contain hidden or undocumented features, or are misleading to consumers in ways such as manipulating them into making a purchase.
Having a trusted app ecosystem, and a robust app review process is critical for enabling a trusted environment that can foster competition across and between apps. It helps give developers a safe and trusted platform on which to build, enables almost immediate global reach, while minimizing the time that developers must spend on implementing security and privacy protections because they have already been built into the device, into its operating system, into its app review process and guidelines, and into the tools that consumers use to control their smartphones.
A number of federal agencies have focused on the importance of ensuring a safe and secure app ecosystem. For example, the Department of Homeland Security’s Science and Technology Directorate has observed:
“Third-party stores also exist . . . but the reliability and security of apps from these sources may vary widely and the vetting process may be opaque or less robust than is the case for the public stores of OS vendors. . . . [U]sers should avoid (and enterprises should prohibit on their devices) sideloading of apps and the use of unauthorized app stores.” Study on Mobile Device Security (April 2017)
Third party app stores often lack the same incentives to protect user trust, privacy and security. This lack of robust app review may be why security firm PurpleSec, found: “Third-party app stores host 99.9% of discovered mobile malware.” These threats are manifested because of a lack of consumer protection guidelines, incentives and lack of a thorough app review process. They also materialize because third party app stores, unlike official app stores tied to a mobile device brand, do not compete in the marketplace based upon their privacy or security protections. The unvetted apps that third-parties host often exhibit security, privacy, or tracking properties which would not be acceptable to the official app stores. These unvetted apps, although still in the minority, can be gateways for malicious code, and can be used by malicious actors to steal financial information, track the device owner, or for the surveillance of communications. In fact, Nokia’s 2021 Threat Intelligence Report found virtually all malware on mobile devices gets there through downloads from third-party sources.
Over time, and with each review, the vetting practiced by official app stores has matured and become increasingly sophisticated. At the same time, reviewers identify a broader range of actors with increasingly sophisticated schemes designed to exploit user privacy, or trick them into new forms of consumer scams. This has led to considerable investment by the official app stores, and an increasingly robust and sophisticated review process.
Like app developers, official app stores benefit from having a rigorous screening process. A broad and expansive marketplace filled with a diverse range of trustworthy apps can provide an obvious competitive advantage in the marketplace. With every interaction or download, their brand is on the line. In order to foster a trusted app ecosystem, both Apple and Google discourage users from “sideloading” unvetted apps from outside of official app stores, and Apple specifically prevents it.
As the FTC points out in its consumer guidance, only downloading from official app stores can be an important consumer privacy protection. The recent 2021 action by the FTC against SpyFone, illustrates how app screening by official app stores protects consumers. In this case, the app at issue was not approved by official app stores but instead had to be downloaded from a third-party website onto mobile devices that allowed sideloading. Once downloaded, the app then “surveilled physical movements, phone use, online activity through hidden hack that exposed device owners to stalkers, abusers, hackers, and other threats,” according the FTC. The FTC found “The company’s apps sold real-time access to their secret surveillance, allowing stalkers and domestic abusers to stealthily track the potential targets of their violence.” They found “SpyFone’s lack of basic security also exposed device owners to hackers, identity thieves, and other cyber threats.” This is the kind of nefarious app and app features that app stores are designed to review, identify
and reject. Consumers that chose devices that don’t allow sideloading of apps were protected from this malicious SpyFone app, because it had no way to get on the phone.
In 2020 alone, one major app store reported it removed or rejected roughly one million malicious apps including 215,000 that committed privacy violations, 150,000 engaging in spam or misleading users, and 48,000 that contained hidden or undocumented features. Having a robust app store review process that can act in advance before a spyware app can get onto a device is much more beneficial to consumers than having to rely solely on a lengthy FTC enforcement action against harmful apps after the fact – especially given the vast number of apps that now make up the app ecosystem. Likewise, preventing consumers and enterprise users from inadvertently downloading, or being tricked into downloading, a non-vetted app from outside of app stores is a security practice that helps protect consumers and enterprise users.
Given these potential harms, the agency charged by Congress with developing cybersecurity practices – NIST – suggests that any sideloading capability should be disabled to protect enterprise users of mobile devices:
“This process of nonstandard installation also is known as sideloading and if done incorrectly could make a mobile device extremely vulnerable to attack. To mitigate against these potential attacks, the sideloading functionality should be disabled when not used for installing the wrapped apps.” Draft NIST Special Publication 800-124, rev. 2, Guidelines for Managing the Security of Mobile Devices in the Enterprise, 2020.
Like other federal agencies, NIST also warns of the security threats posed by third-party app stores:
“Application stores pose an additional threat vector for attackers to distribute malware or other harmful software to end users. This is especially true of third-party application stores not directly supervised by mobile OS vendors. . . .” Draft NISTIR 8144, Assessing Threats to Mobile Devices & Infrastructure: The Mobile Threat Catalogue (2016)
A CONTINUOUSLY ADAPTING MOBILE ENVIRONMENT IS ESSENTIAL FOR FOSTERING A TRUSTED ENTERPRISE APP ECOSYSTEM
While technology moves rapidly, new cybersecurity threat vectors can emerge on the scale of weeks, days, or even seconds. In a dynamically changing enterprise environment, delayed response can mean the difference between averting an exploit or losing tens of millions of dollars. To protect users, major technology companies invest billions of dollars a year into driving security into their products and services,
and reinforce and enhance this by building and running large, sophisticated, product security teams which work 24×7 to identify, understand, and ameliorate risks in the constantly changing security treat landscape. Government enforcement actions against bad actors can be critical, but also take much longer than a technology company working to stamp out a new threat.
Given the realities of the cyber threat landscape, and the fact that mobile devices are used by enterprises, critical infrastructure, and military and intelligence networks, policymakers should avoid forcing mobile device manufacturers to introduce cyber risk into the ecosystem, and accept unvetted apps onto the device. through the introduction of unvetted apps.
Specifically, policymakers continue to follow federal guidance, and prevent the sideloading of unvetted apps or use of unofficial third-party app stores.
Examples of federal agency mobile app guidance include:
For federal employees, the General Services Administration indicates that “[i]nstallation of applications from unknown sources is not authorized,” requiring government users to only download apps “through approved methods (provided with the operating system – Apple iTunes and Google Play respectively).” The GSA explains that “[a]llowing mobile apps to be loaded from an unknown source presents one of the greatest risks to GSA’s environment when using mobile devices.”
- The National Security Agency recommends: “Install a minimal number of applications and only ones from official application stores.”
- DHS’s Science and Technology Directorate: “[U]sers should avoid (and enterprises should prohibit on their devices) sideloading of apps and the use of unauthorized app stores. Android’s built-in Verify Apps feature or third- party, mobile threat protection solutions for both Android and iOS can help identify potentially harmful apps installed on devices.”
- The FBI’s Criminal Justice Information Services Division, recommends against using a device capable of being configured to sideload:
“One of the few effective attack vectors to compromise mobile operating systems is to manipulate the device user to install a malicious application. . . . Unsigned or un- trusted apps are cryptographically prevented from executing on non-jailbroken iOS devices. . . . On either platform it is highly desirable to limit allowable applications to a pre-approved pool of apps via MDM or organizational App store structures and device policy.”
The FBI reports that Internet crime is on the rise. It’s recently released 2021 Internet Crime Report found that in 2021, “America experienced an unprecedented increase in cyber-attacks and malicious cyber activity.” The category with the highest victim count involves “Phishing/Vishing/Smishing/Pharming” which the FBI defines as “[t]he use of unsolicited email, text messages, and telephone calls purportedly from a legitimate company requesting personal, financial, and/or login credentials.”
Specifically targeted at mobile phone users, smishing is the technique of using SMS messages to send texts which trick the user into clicking on a link which can then encourage them to give up their financial account login credentials, private information, or take them to a site that downloads malware on their device. The fact that Smishing is on the rise, reflects the widespread adoption of smartphones and the significant amount of sensitive financial and personal data stored on these devices. In fact, our own recent survey found that two-thirds of respondents report that they personally have received a text message from either an unknown sender or an illegitimate one claiming to be legitimate and asking them to click on a link. This is consistent with other research.
In recent months, the FluBot criminal campaign and other smishing campaigns have swept through Europe and Australia, attempting to trick the user into clicking on a link that sounds attractive, and time sensitive — like checking the status of a package or signing up for a COVID-19 vaccine appointment. If the device allows sideloading, once the user falls for the scam, clicking on the link will result in a malicious code being downloaded to the device. If the device does not allow sideloading, the criminal’s attempt to install the malicious app will fail. In its complaint against SpyFone, the FTC specifically noted how consumers were tricked into disabling certain mobile device security features in order to download the nefarious app from outside of official app stores.1
Consumers should not be expected to have to have the same level of knowledge as a Chief Information Security Officer of a company to be able to maximize the benefits of mobile innovation. Our own surveys show that consumers are often not taking all of basic cyber-hygiene best practices that federal agencies and experts in the field commonly suggest they adopt. We need to help consumers follow these best practices. But we should also support consumers, if they so desire, to be able to choose a mobile device in the marketplace designed to protect their safety, security, and privacy by design out of the box. Consumers should be able to choose devices that provide consumer focused tools, adopt robust safety, privacy and security guidelines, and employ a rigorous review processes designed to protect consumers and build the basic trust necessary for the entire mobile ecosystem to grow and thrive.
TRUSTED MOBILE OPPORTUNITY IS CRITICALLY IMPORTANT FOR DRIVING BREAKTHROUGH OPPORTUNITIES AND ENTIRELY NEW FORMS OF COMPETITION IN NEW PARTS OF THE ECONOMY.
Some of the biggest opportunities over the horizon that can come from a vibrant, innovative and competitive mobile ecosystem will come in sectors of the economy that have yet to be fully transformed by the Internet. It can create new competition in entirely new app categories. It can create new types of business models in traditionally stymied industries. And it can help new upstarts compete in more traditional parts of the economy. However, at the point of convergence between our virtual and physical worlds, as the mobile app ecosystem begins touching more of the physical sectors of the economy – manufacturing, transportation, agriculture, and health care for example – a trusted app ecosystem becomes increasingly important for achieving important gains.
- In manufacturing for example, Accenture estimates that 5G-enabled factories can see up to 20- 30% in overall productivity gains, including improvements of 50% in assembly time, 20% in asset life, and 90% in defect detection. Factory floors are now increasingly being controlled with tablets running innovative apps that help manufacture products with digital precision, improve worker safety, and boost factory floor efficiency. But companies are also unlikely to make this digital transformation at a time when ransomware has the ability to shut down production lines, and as ransomware attacks in manufacturing are on the rise — tripling in 2020. They need a trusted mobile app ecosystem.
- In transportation, Accenture estimates that new connected vehicle technologies have the potential to reduce the severity of non-impaired crashes by 80%, save $3.6 billion in collision costs, and reduce traffic by 25%. Already at the heart of connected cars, more than 80% of new cars support in-dash apps connected to the mobile app ecosystem including Apple’s CarPlay and Android’s Auto, and several other competitors which together extend the mobile app ecosystem directly onto the car’s dashboard – and bring necessary competition directly to traditional navigation systems tied to vehicle manufacturers. But lack of trust could slow down these opportunities as cybersecurity attacks emerged as the top concern for 63 percent of automotive and technology executives in developing technology for connected cars and autonomous vehicles. They need a trusted app ecosystem.
- In healthcare, smart watch and phone sensors are saving lives as new advances in mobile devices and apps are demonstrating they can detect diabetes with 85% accuracy rate, sleep apneas with 90% accuracy, hypertension with 82% accuracy, and abnormal heart rhythms with 97% accuracy. McKinsey estimates that connected digital devices could help cut the costs of chronic disease treatment by as much as 50 percent. But according to Accenture’s Digital Health survey the top ranked concern about using digital health tools (38%) is privacy and data security followed by a lack of trust in the technology. People are less likely to take advantage of potentially lifesaving apps and connected devices if they don’t trust that their privacy will be protected and their devices can be secure. They need a trusted app ecosystem.
- In agriculture, the mobile app ecosystem is helping grow a precision farming revolution that has the potential to cut water use by up to 30%, reduce herbicide use by 99.99%, reduce fuel use by 10%, and cut food prices in half. Already 9 out of 10 farmers now use a smartphone in their combine. Tablets are frequently used to run Decision Support Systems to control their farming assets or to control drones that survey the fields. Smartphones are also used today to alert dairy farmers of changes in the vital signs of their herd, help farmers predict future weather and its impact on irrigation, and smart apps can help farmers identify plants and weeds in real time. But a DHS/ USDA sponsored analysis has identified, privacy and security as top concerns of farmers considering implementing precision agriculture techniques. The FBI recently reported that attacks on the agriculture industry are increasing, with at least eight major attacks on agricultural companies in 2021 alone including the international meatpacking company JBS, and an attack on an Iowa grain co-op that nearly crashed the grain market. Farmers are unlikely to adopt these transformative new technologies, if farmers aren’t able to trust that their privacy will be protected, and their devices can be protected from security exploits or malware that could shut down their production. They need a trusted app ecosystem.
In each case, having a trusted mobile app ecosystem is essential for unlocking the vast societal opportunities that can continue to come from an innovative and dynamic mobile app ecosystem.
RECOMMENDATIONS:
- Apply a Common-Sense “Trust Screen” To Any Proposed Changes. We encourage NTIA, other stakeholders, and policymakers to apply a ‘trust screen’ to any proposed policies or questions, and ask a simple question – would this policy enhance or undermine trust in hardware, software, products, services or the digital ecosystem?
- Support Baseline Privacy Protections and Encourage Privacy Leadership. Consumers deserve an app ecosystem where privacy protection is a basic right, where clear boundaries exist around what can be collected, processed, tracked and shared, and where users have the tools they need to control their own data. Policymakers should continue to support and encourage innovation and leadership in the mobile marketplace to improve transparency, increase consumer control, and help consumers make more informed marketplace choices. The Administration should also commit to supporting and advancing a comprehensive national privacy framework that establishes uniform privacy expectations and ensures all entities in the app ecosystem have the same level of commitment to consumer privacy.
- Foster Robust Cybersecurity Safeguards and Work to Fill the Cyber Talent Pipeline. Robust security is at the heart of unlocking even greater app economy potential. At a time of heightening cyber risks, it is more important than ever that policymakers continue to encourage continuous security innovation that can help protect the entire app ecosystem. It is also critically important to advance comprehensive federal efforts to fill the cyber talent pipeline, and close the cyber skills gap.
- Crank-up Our Innovation Ecosystem With Continued Federal Investments in the Future. Federal investments in basic research and innovation have been essential for advancing today’s innovative mobile ecosystem, and will be even more essential for tomorrow’s. DARPA investment in basic research led to GPS, the Internet, Siri, and speech recognition. NSF investments in basic research led to the Internet browser, the search engine, and touchscreens – all of which are essential ingredients for the mobile ecosystem we enjoy today. We support the Administration’s effort to advance the Bipartisan Innovation Act which will help us invest in the next wave of technological breakthroughs to drive an even more dynamic and trustworthy mobile ecosystem, and believe it is the most important technology related bill that Congress can and should pass this year.
